Banking apps are the real flag bearers for a reputable and respected bank because banking is a severe business. They must be carefully tested because mobile...
Are you struggling with writing email validation test cases? It’s time to show those pesky typos who’s boss. In this blog, I’ll provide tips and tricks...


In many cases the primary cause of software StartUp failure tends to be poor quality assurance during the development process, this is where end-to-end testing can...
Anyone who owns an iPhone, iPad, or iPod Touch has heard this word at least once. And anyone who is interested in IT is probably familiar...

This tutorial will show you how to create email validation test cases. Many applications will collect your email ID. You can purchase tickets, schedule an appointment,...

The search function in the app enables users to search digital objects in the collection through simple search or advanced search. A search function that searches your...
It is a common problem for Android devices to not be able to connect to the internet. Not so often, now in the Era of LTE...


It’s a kind of software testing used for verifying the functionality of the applications software application. Functional testing involves testing functions with values, estimating the output...
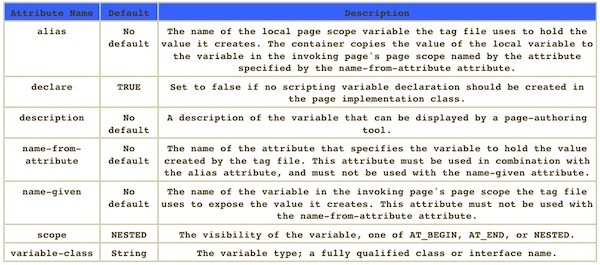
In this article, we will help all the Web Developers to get started with JavaScript and JavaServerPage. Java Server page is often used at the development...
When you install Windows 10, it prompts you to set a password. However, skipping this step is common and many people choose not to do so....
Snapchat is one of the most popular social media apps in the market. Teenagers widely use it and young adults to chat, share photos, videos, put...
Discord is a chat platform that is used by gamers around the world. The users can easily interact with other users by creating servers within the...
Have you ever encountered a situation where you want to copy an inspiring quote or inspect a particular element, but the right-click menu simply doesn’t work?...


Each time a user purchases a phone, they’re assigned with an IMEI number. This stands for ‘International Mobile Equipment Identity’. The IMEI is there to identify...
Keeping Windows OS update is always recommended, and we need to do it properly. However, sometimes Windows update files come with some issues in some programs....

Discord is the easiest way to talk over voice, video, and text. Talk, chat, hang out, and stay close with your friends and communities. Open Discord official...

A collection of the best Mobile test automation tools than you can use to test your Mobile Apps. For iOS and Android Only Android Solutions Best...